Just imagine you are an accountant working late into the evening during tax season. You have dozens of client files open, deadlines to meet, and suddenly your system freezes. Then to add stress to the situation a virus alert pops up on your screen. This is a nightmare scenario that no accountant or finance company wants to deal with . When sensitive client data is on the line, even a small security breach can cause serious financial loss and reputational damage. Not to mention the disruption to your team scrambling to address the problem.
To mitigate against these kinds of instances Hosted Desktop services come into play, providing reliable, secure, and 24/7 available access to your work environment, from anywhere, at any time.
What is a Hosted Desktop?
Think of a hosted desktop as your entire office computer, but instead of being physically in your office, it lives and runs on the internet (in the cloud). Instead of relying on one device, your desktop files, applications, and software are all stored in a secure UK data center. Log in from any internet-enabled device and work as if you are at your office desk.
For modern accountants and financial firms, this offers a major benefit. There’s certainly no need to carry confidential data on a USB stick, or risk losing files if your laptop fails. Everything is securely stored in the data center and managed by IT specialists.
Why Security Matters for Accountants
Accountants and finance firms deal with a high volume of highly confidential information. From tax returns to payroll data, your reputation depends on keeping that information secure. A single breach could cost far more than the price of any reputable IT service.
That is why hosted desktop services for Accountants and financial firms in Manchester place such a strong emphasis on security. Venom IT adds several layers of protection, so your client data is safe from any risks at each stage. Let’s look at what this includes.
Key Security Features with Venom IT Hosted Desktop Solutions
Our Hosted Desktop and Citrix services offer core security attributes for accountants and finance enterprises, which include the following:
- Sentinel One Endpoint Protection – This provides AI-driven endpoint protection that immediately detects and stops suspicious system actions, preventing malware, ransomware, and other virus attacks before they cause harm to the system.
- Duo Two-Factor Authentication (2FA) – This feature requires users to complete an extra login step, similar to approving access from their phones, which would allow only authorized individuals to access your hosted desktop.
- Data Centers in the UK- All your data is stored within the UK data centers, keeping your business aligned with GDPR and fiscal compliance norms.
Hosted desktops for Accountants and Finance firms make hybrid-working much simpler and safer in numerous ways, such as:
- Work from anywhere – You can access your desktop securely at home, at the office, or indeed while hanging out.
- No need to invest in new hardware systems – Your desktop is in the cloud, so you do not need to keep buying new computers and laptops.
- Scheduled backups – If your device crashes, your work will remain safe as before.
- Fast and reliable performance – Venom IT guarantees high availability, allowing minimal downtime for your team.
- Scalability – Add new users or increase the storage easily as your enterprise grows.
Why does Venom IT’s Hosted Desktop Services stand out from others in the Manchester IT Market?
Due to the integration of Sentinel One’s advanced threat protection and Duo 2-Factor Authentication, Venom IT provides a strong shield to your business against Cyber attacks. We provide 24/7 support whenever you need help. With ISO 27001, 27017, and 27018, as well as other Cyber Essentials certifications, Venom IT meets industry standards. Also, our transparent SLAs clearly guarantee uptime and efficient performance.
What to do next?
In the fast-paced world of finance, uninterrupted operations, strong data security, and seamless regulatory compliance are essential for accountants and financial professionals to carry out their tasks smoothly. With advanced AI tools, Venom IT ensures your firm is not only productive but also protected against cyberattacks.
For a smarter way of working, with improved digitized technological tools, our Venom IT’s Hosted Desktop services would be the best solution for your firm to reach new business heights.
To find out more about how we can help your finance team, simply get in touch with an expert here: https://venomit.com/contact-us/
Cloud computing refers to a collection of online services that offer businesses a cost-effective solution to increase their IT capacity and functionality. Businesses can choose what sort of cloud computing solution fits their needs. They can choose where, when and how they use cloud computing to ensure an efficient and reliable IT solution. (more…)
So, that’s our full explanation of digital transformation – all in a single infographic for you. Moreover, be sure to click on it and download the entire graphic so you have it to hand (it’s a PDF). As you probably know already, we go the extra mile for you here at Venom IT, too. In fact, we’ll give all this information to you in words as well.
Read on to see a written explanation of a digital transformation process.
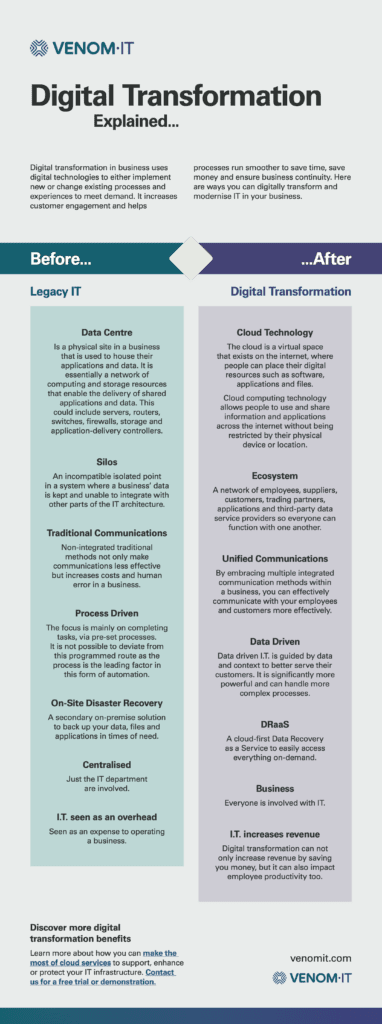
Digital Transformation Explained
Digital transformation in business uses digital technologies to either implement new or change existing processes and experiences to meet demand. It increases customer engagement and ensures processes run smoother in order to:
- save time;
- save money and;
- ensure business continuity.
Below, we share several ways you can digitally transform and modernise IT in your business, and contrast them with the old processes that will undoubtedly feel dated and out of touch with your needs moving forward.
BEFORE: Legacy IT
Data Centre
Data centres are physical sites in a business that house all of the business applications and data. It is essentially a network of computing and storage resources that enable the delivery of shared applications and data. This could include servers, routers, switches, firewalls, storage and application delivery controllers.
Silos
Silos represent an incompatible, singular point in a system where you store business’ data. Additionally, that system is unable to integrate with other parts of the IT architecture
Traditional communications
Non-integrated traditional methods not only make communications less effective but increases costs and human error in a business.
Process Driven
The focus is mainly on completing tasks, via pre-set processes. It is not possible to deviate from this programmed route as the process is the leading factor in this form of automation.
On-Site Disaster Recovery
A secondary on-premise solution to back up your data, files and applications in times of need.
Centralised
In short, within a centralised system, only the IT department got involved.
IT is viewed as an overhead
Seen as an expense to operating a business
AFTER: Digital Transformation
Cloud Technology
The cloud is a virtual space that exists on the internet, where people can place their digital resources such as software, applications and files.
Cloud computing technology allows people to use and share information and applications across the internet without being restricted by their physical device or location.
Ecosystem
A network of employees, suppliers, customers, trading partners, applications and third-party data service providers so everyone can function with one another.
Unified Communications
By embracing multiple integrated communication methods within a business, you can effectively communicate with your employees and customers more effectively.
Data-Driven
Data-driven IT is guided by data and context to better serve their customers. It is significantly more powerful and can handle more complex processes.
DRaaS
A cloud-first Data Recovery as a Service allows for easy access to everything in an on-demand environment.
Business involvement
In effect, everyone is involved with IT.
IT increases revenue
Digital transformation can not only increase revenue by saving you money, but it can also impact employee productivity too.
Learn more about our Business Continuity series
Follow the link below for an infographic of what a good disaster recovery and business continuity plan should look like. You can also discover some more of our insights on digital transformation, and expert guidance on the key platforms your business relies on:
- Infographic: Business Continuity & Disaster Recovery Comparison
- Brand Battle: Citrix vs Azure.
- Brand Battle: VMware vs VirtualBox.
Learn more about how you can make the most of cloud services to support, enhance, or protect your IT infrastructure. Contact us for a free demonstration.
Check out our cloud computing infographic: be sure to click on it and download the entire graphic (it’s a PDF, just so you know). We go the extra mile for you, too: we’ll give it all to you in words below. (more…)
Web hosting can be an intimidating topic to know where to start. Firstly, do you know what the differences between Cloud Hosting and Hosted Services are? Luckily for you, we’ve organised the differences in a handy graphic: be sure to click on it and download the entire graphic (it’s a PDF, just so you know). (more…)
So, there’s the infographic: be sure to click on it and download the entire graphic (it’s a PDF, just so you know). But we go the extra mile for you, too: we’ll give it all to you in words below.
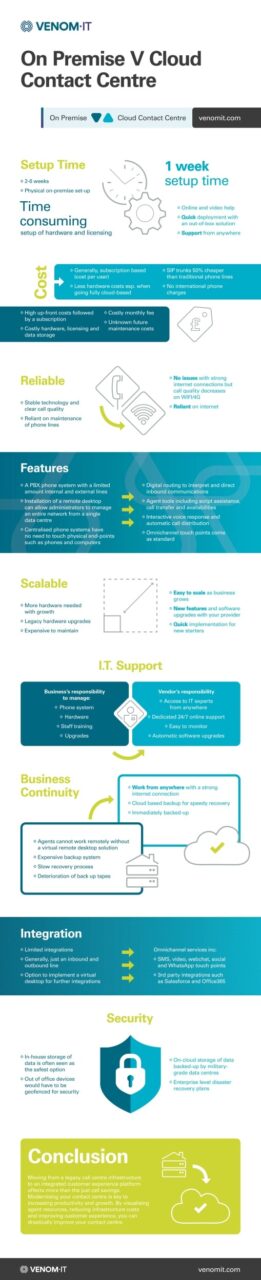
Head to Head: On-Premise vs Cloud Contact Centre
On-Premise |
Cloud Contact Centre |
|
Setup Time |
|
|
Cost |
|
|
Features |
|
|
Scalable |
|
|
Reliable |
|
|
Business Continuity |
|
|
Integration |
|
Omnichannel services include:
|
I.T. Support |
Business’s responsibility to manage:
|
Vendor’s responsibility
|
Security |
|
|
Learn more about On-Premise vs Cloud Contact Centre comparison
For more information about choosing the right CCaaS provider and the benefits of cloud-based contact centres, check out our resources below:
- Whitepaper: The best contact centre statistics for your business case.
- Brand Battle: RingCentral vs 8×8.
- Brand Battle: 3CX vs Vonage.
- Case Study: Ashley Helme Associates.
Learn more about how you can make the most of cloud services to support, enhance or protect your IT infrastructure management. Contact us for a free trial or demonstration.
Disaster recovery vs business continuity, how do they differ? We’ve produced an in-depth guide of risk and benefits across 7 key elements for both services.
Head to Head: Business Continuity/Disaster Recovery Comparison
Business Continuity |
Disaster Recovery |
|
Definition |
Business continuity is a long-term plan which outlines how your organisation should act during and after a disruption or disaster. | Disaster recovery is a strategy which reduces the impact of a disaster and facilitates the recovery of critical IT systems. Disaster recovery as a service can also be outsourced to a third party provider to ensure greater results. |
Business Aspects |
There are 3 main types of risk:
Business continuity is more strategic and looks at sorting and prioritising risks, and preemptively avoiding or reducing risks. |
Disaster recovery focuses on restoring IT systems so organisations can return to full functionality.
Disaster recovery plans usually include a ‘playbook’ of procedures that should be initiated under specific circumstances. Disaster recovery leans itself towards risks that can be mitigated (e.g. DDoS attacks, or nation-state attacks) and unavoidable threats (e.g. flooding or fire). |
Risk Factor #1 |
Cyber SecurityIn our modern world, the prevalence of cyberattacks is undeniable. Hundreds of organisations experience data breaches on a daily basis, and the consequences range from financial losses all the way up to legal action and reputational damages. Therefore, robust cyber security solutions are no longer an option, they are simply a necessity. |
Theft of dataThe increasing prevalence of remote working has also increased the amount of sensitive data being accessed from employee’s personal devices. This adds an additional layer of vulnerability, as staff may “accidentally” share or compromise this information. |
Risk Factor #2 |
Physical securityIf you don’t know what’s in your security system, you won’t be able to protect it. From video surveillance to fire alarms, make note of every aspect of your physical security to ensure you can enhance the overall safety of your premises. |
VirusesThe most common culprit behind massive data loss often stems from malicious attachments or viruses embedded in emails In this scenario, data backups are crucial because they ensure any lost or compromised information is restorable. |
Risk Factor #3 |
Economic and financial risks675,000 businesses have fallen victim to fake invoice fraud in the UK*. Businesses need to fortify their security stance by putting t in place policies, tools and systems that enable business continuity. |
Malware and ransomwareMalware affects systems, backups and storage. It’s an increasingly common issue in which malicious actors hold sensitive data or critical systems hostage and organizations are confronted with the ethical dilemma of paying the ransom. Many cyber insurance companies will cover this cost; however, putting money into the pockets of criminals may encourage future attacks. |
Risk Factor #4 |
ComplianceBusiness continuity plans don’t always prioritise compliance and risk systems; however, industry regulators are now fining companies for non-compliance regardless of any other disruptions organisations may be facing. |
Cyber-attacksA post-incident report will expose the root cause, impacted areas, and the extent of the damage. This comprehensive analysis will ensure no lingering vulnerabilities are putting your organisation at risk. |
Risk Factor #5 |
Unsecured networksUnsecured networks are those that lack any sort of protection, leaving data unencrypted and information vulnerable to potential hacking. The main goal is to ensure the network and data is restored as rapidly as possible. |
Natural disasters and pandemicsFrom fires and floods to unforeseen events like the COVID pandemic, all types of natural disasters should be accounted for in your disaster recovery plans. Whether you rely on remote desktops or cloud backups, it’s crucial that your recovery plan remains up-to-date, regularly practiced, and subjected to routine testing. |
Risk Factor #6 |
Accidental deletion of dataIt happens to the best of us. One wrong click of a button and all your data disappears. Thankfully, most cloud storage systems automatically back up data and allow for a seamless reversal to previous reiterations. |
ReputationDocumenting business continuity during the recovery process can help organisations manage customer expectations and sentiments, which, in turn, helps preserve reputation during hacking incidents. |
Risk Factor #7 |
Human errorYour employees are your first line of defence against the threat of malicious hackers; however, many companies fail to train their staff correctly. Since human error accounts for almost half (47%) of all major IT mistakes, investing in ample training opportunities is of the essence. |
Learn more about our Business Continuity vs Disaster Recovery series
Follow the link below to see what a comprehensive disaster recovery and business continuity plan should look like. You’ll also discover more of our insights on digital transformation, and expert guidance on the key platforms your business relies on:
- Infographic: Digital transformation explained
- Brand Battle: Citrix vs Azure.
- Brand Battle: VMware vs VirtualBox.
To learn more about cloud services and how they can support, enhance, and protect your IT infrastructure, simply take a look at our case studies or contact us on 0330 202 0220 to request a free demonstration.
Our full infographic comparing business continuity and disaster recovery (below) is available to download here: