How to Set Up and Maintain a Reliable VoIP Infrastructure
Now more than ever, you must consider switching from traditional analogue phones to VoIP systems. VoIP is the future of communications. It is cheaper, faster, and more efficient than conventional phones. It also ensures seamless communication between you and your remote team. Surprisingly, the transition from analogue phones to VoIP has not been as drastic as we hoped. One primary reason is many businesses have a false notion that a VoIP infrastructure is complicated and expensive, so why bother? Well, that is true if you don’t select the right VoIP provider or set up your VoIP phone system in a way that lowers your upfront costs. So, in this blog, we will show you how to maximize the benefits of your VoIP phone. Let’s get started.
What to opt for in a VoIP Infrastructure
Your VoIP phone system should have the highest quality standards and be reliable. Unfortunately, many people do not know what to look out for in a VoIP phone and waste time and resources. Here is what you need in VoIP management.
- Prompt response time
- Consistent call quality
- Notifications and updates
- Security and data protection
- Smooth system uptime
How to Prepare for a Successful VoIP Infrastructure
You need to have a planning process for a seamless VoIP experience. Here is your to-do list when building a VoIP infrastructure.
- Know what your company needs
- Get the proper setup for a network
- Get a backup communication plan
- Train your team to use the system
- Test your VoIP infrastructure, monitor performance, and make necessary adjustments.
How to Set Up and Maintain a Reliable VoIP Infrastructure
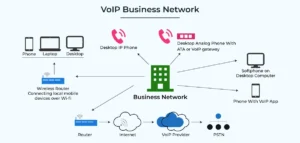
After the planning process, there are some things you need to figure out to ensure you get the most out of your VoIP system.
Have a Stable Internet connection and network.
Unlike analogue phones that communicate through electrical signals and telephone lines, VoIP transmits messages via digital signals and the internet. So without capacity, it will be impossible to use a VoIP infrastructure. So it is essential to load up enough data bandwidth for your VoIP system to run smoothly.
But how much bandwidth do you need? Experts say you need at least 100kbps upload and download per line. Although you can rely on your home internet or Wifi, they may have slower upload and download speeds. So we recommend hiring internet service providers because their stable connections will ensure you can use your VoIP phone without jitters.
Other internet options like microwaves are unstable and will affect the VoIP call quality. Unfortunately, an unreliable internet connection can’t handle traffic, resulting in dropped calls and low-quality audio. So conduct a VoIP speed test to know if a VoIP infrastructure will operate efficiently on your internet bandwidth. We recommend configuring your Quality of Service (QoS) to prioritize your voice traffic over channels like Netflix.
Invest In The Right VoIP Hardware
VoIP infrastructure is only as good as the hardware you use. So after securing a stable bandwidth, research the innovative VoIP hardware on the market. For the best value, you can purchase VoIP desk phones like Polycom VVX601 and Cisco 7841.
Another invaluable tool you need is a VoIP headset to move around while still on your phone. But to lower your costs, buy an Analog Telephone Adapter (ATA) so all your analogue phones can function as VoIP phones. The adapter converts analogue signals into digital signals to enable communication between your phones and the network. It is also easier on your employees because they know how analogue phones work.
Finding a VoIP Provider with the Features Your Business Needs
Debra Hamilton, a communication expert, says companies can lose 100 employees or $420,000 annually because of miscommunication. It means the stakes are high regarding choosing a VoIP provider.
There are many VoIP providers, but not all will meet your business needs. Your VoIP provider should give a CRM with unified communications so you can efficiently communicate with team members at every turn. They should also have cross-department channels and call analytics so you can better use your resources and send tailored messages to your customers. So consider all these factors to hire a VoIP service provider that best suits your business goals.
How To Get a VoIP Business Phone Number
Most VoIP packages and plans come with a local phone number. You can also port any business number already in use. But if that isn’t the case, there are other options for getting a phone number.
Types of phone numbers
- Local phone number: Local numbers are convenient for small businesses because of their proximity to local customers. You can get a local number for free or pay $10/per month.
- Toll-free numbers: A toll-free number is much preferred among customers because it is free and makes your business look reputable and professional. You will pay $10 per month for your toll-free phone number.
- Vanity numbers: Vanity numbers easily stand out because they include a toll number and specific words describing what you do. They are expensive and can cost between ten to fifteen dollars per month. You can purchase a vanity number from VoIP service providers or third-party vendors like NumberBarn.
How to Set Up Your VoIP Phone System
It is the most crucial stage, and your VoIP phone system will depend on the number of employees using the infrastructure and hardware. Luckily, some service providers sell ready-to-use VoIP sets. So with a standard network switch and a Power over Ethernet (PoE), you plug it in and use it. However, if you do not have that luxury, you can follow our steps to set up your VoIP infrastructure.
- Insert the AC adapter into the socket, then attach it to the phone or the handset base.
- USE a CAT5e or CAT6 cable to link the IP phone to the switch or router.
- Listen for the dial tone after the connection has initialized.
Connecting VoIP desk phones to PoE-enabled routers
- Use Ethernet cables to connect the phones to the PoE-enabled switch or router.
- Switch your phone on, which should link to your service provider.
Set Up Your VoIP Headsets
When buying VoIP accessories like headsets, always get modern ones that can connect to Electronic Hook Switch (EHS) cables.
How to set up VoIP headphones with EHS cable support:
- Insert the AC adapter and base of the headset into an outlet.
- Plug an EHS cable into the headset’s base unit.
- Connect the other ends to your desk phone, headphone network port, and EHS port
- Verify the connection by pressing the call control button.
Test Your VoIP Lines
It is time to know if your internet connection, VoIP accessories, and set-up will coordinate. Test your VoIP line by making several calls to check the audio quality, connection stability, and latency.
Test the following qualities of your VOIP line:
- Audio quality: Can you hear someone speak clearly and consistently?
- Latency: Are there any delays between speaking, the receiver hearing, and the response?
- Connection stability: Did the call drop at any point? Was there lagging between making and ending the call?
Train Your Staff to Handle VoIP Management.
It may be the first time some of your employees have heard of ViOP, much less know how to use it. So it is essential to train them to use the VoIP phone system features like forwarding voicemails to email and recording cloud calls. Take this seriously because when you introduce employees to new technology without instructions or a manual, they will fall back to old methods. If you experience any difficulties getting your employees on board, you can contact the customer support of your VoIP providers to assist.
Things That Hinder VoIP Infrastructures
VoIP isn’t perfect because it has components prone to fault or failure. Here are some things that can prevent your VoIP software from optimal performance.
- Blocked ports: Blocked ports cause voice services to malfunction, resulting in low-quality audio.
- Access lists: Access lists are rules which determine which user or resource can or cannot access a system. There may be instances where ACL rules block a packet from reaching an IP address.
- Firewall rules: Firewalls, like access rules, protect your network from data pickets that may not be secure enough.
- Voice traffic: VoIP ports enable you to communicate with your team, but blocked ports have no audio or one-way audio.
A VoIP phone system is flexible and allows remote workers to work from anywhere as long as they have an internet connection, eliminating the need for expensive office space and equipment. VoIP infrastructure has revolutionized how we work and enabled businesses of all sizes to operate and collaborate without the need to be in the same physical space. These should be reasons enough to join the future of communications and remote work.
It’s no secret that the world of work is changing. More and more people are working remotely, and this trend will continue. It means your employees will spend less time in the office with you, making it challenging to collaborate as a team. A VoIP phone (Voice over Internet Protocol) allows you to communicate with your employees remotely. It can help keep everyone on the same page even if they are not physically present at meetings or other events.
From enabling remote work to improving communication, VoIP phones for business are shaking up how we work and communicate in the 21st century. With a VoIP phone, employees across distances can cut the cord and take their conversations global. They can collaborate in real time while enjoying cost-saving benefits like free calls and unlimited texting. VoIP is not just the future of work– it is already here and reforms how we stay connected!
In this blog post, we will explore how the service is changing how we work remotely and communicate with each other.
The Role of VoIP in the Future of Work and Remote Communication
The future of VoIP is here, and it’s not what you think. It’s not a call with a robotic voice that tells you to press “1” if you want to speak to a human.
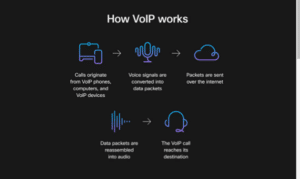
So what is VoIP? It stands for Voice over Internet Protocol and is another way to make phone calls using your computer or mobile device. Instead of using traditional landlines, you can use your VoIP phone to send voice signals from one computer to another. It makes it possible for you to talk with anyone with access to an internet connection. Since most people have access today, you can connect with practically anyone on Earth!
The future of VoIP will involve two main things; improved quality and lower VoIP service costs.
Increasing demand for unified communications
Providers have made remote communication more seamless than ever. We can attribute this to the increasing demand for unified communications (UC). Unified communications is an umbrella term for multiple communication tools like phone calls, emails, voice messages and many more.
It can include email, instant messaging and video conferencing—all integrated into a single system.
To understand how VoIP fits into this picture, we need to look at how UC works today:
- Email is king with internal communication within an organization.
- Instant messaging has become more commonplace when communicating with absent coworkers. However, many people still have separate IM accounts for work and personal use.
- Video conferencing has become a common way to meet with colleagues while working remotely.
A VoIP phone is the perfect solution for unified communications in remote working. It enables organizations to connect managers, employees, and customers seamlessly and cost-effectively. Service providers offer more than just audio-visual communication. VoIP phone service also unifies all aspects of communication, regardless of location.
5G-improved quality of service
The role of VoIP communication in the future of work is invaluable. 5G technology allows for a massive leap forward in VoIP quality, with dramatically improved connection speeds, sound clarity and lower latency. Not to mention, businesses can benefit from the cost savings associated with VoIP too. It all adds up to an enhanced remote working experience. It will change how we work, making remote communication faster, easier and more efficient.
Interactive voice response (IVR)
The VoIP phone has an interactive voice response (IVR) technology that has revolutionized how we do business. IVR lets organizations interact directly with customers without a receptionist or other staff. This feature gives companies more flexibility and cost efficiency. By using IVR, customers can access information more quicker and easier. While businesses can streamline customer service operations, and workers can stay connected on the go.
The IVR system is an AI tool that allows businesses to provide callers/customers with information without speaking to a human representative. It processes and answers customer questions. Then, transfers the caller to the company rep for more detail.
Artificial intelligence (AI) in VoIP
With AI-powered VoIP, businesses can maximize their communication capabilities with existing and potential customers. A VoIP phone uses sophisticated algorithms to offer an enhanced communication experience. It can do this by recognizing speech patterns and understanding context. It ensures that the conversations are smoother, more natural, and more efficient. AI-driven VoIP phone service also makes it easier for workers to access customer information from multiple locations. Thus, it enables them to provide better support in shorter time frames. The ability of AI-enabled VoIP to create more effective platforms for employees to work remotely will restructure how brands do business in the future.
Voice-to-text
Voice-to-text technology works with speech recognition software that can convert spoken words into text. The idea behind this approach is simple. If you can listen to someone or something, you can write what they say without having to write it down manually first! That’s where speech recognition comes in handy. It allows you to convert speech into text at incredible speeds and accuracy without extra hardware like headsets or microphones.
Omnichannel
Service providers will continue to reform the future of work and remote communication. The technology allows for a multi-channelled approach to conversations. It helps you move seamlessly between messaging and social media channels. It means employees can communicate easily with each other, no matter where they are in the world. A VoIP phone’s flexibility allows businesses to scale up quickly and easily. The VoIP phone caters to their growing needs without compromising quality or customer service. With VoIP, the future of remote communication looks brighter than ever.
Conclusion
VoIP communication has made our lives easier and more convenient. It has also changed how we communicate with colleagues, friends, and family. VoIP providers provide a reliable and secure solution that allows you to communicate wherever you are without hiccups.
VoIP is the best solution for remote communication in the future because it provides high-quality voice calls with minimal latency. It also offers several features like call forwarding and call conferencing, which can be very useful in different situations.
A VoIP phone is an incredible asset for businesses and allows you to expand your reach.
It also offers better customer service to those who might not have access to such services. VoIP phone has also allowed workers to spend more time on personal projects or tasks to achieve self-fulfilment.
Voice over Internet Protocol (VoIP) is a cloud-based phone system that sends and receives calls through an internet connection.
VoIP phone systems are an attractive communication solution for businesses. Its functionality and cost-effectiveness have made it popular among small and large companies alike. So, it is essential to ensure the security and privacy of VoIP calls to save your business from huge losses.
This article touches upon the importance of VoIP security and common security threats. We will also discover how to make VoIP calls as secure as possible.
Importance of VoIP Security
A survey carried out among risk management experts showed that cyber incidents are the most common risks to businesses in 2023. Data breaches are very dangerous. They can lead a business to bankruptcy
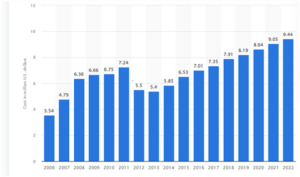
The average cost of data breaches in the US was 9.44 Million US Dollars in the year 2022. This is a considerable rise compared to the numbers of the previous year. In 2021, the average cost per data breach was 9.05 Million dollars.
Many small businesses fail to recover from a data breach. One study found that as many as 60% of small businesses have to call it quits within 6 months of a cyber attack.
Cyber security is one of the top concerns of business owners. If you are switching from traditional landline communication to VoIP calls, you must ensure it is secure and safe.
What are the Common VoIP Security Risks?
Distributed Denial of Service (DDOS) Attacks
The attacker overwhelms the server with data and uses up all of its bandwidth. This results in denial of service i.e. users can’t use their VoIP phone services.
DDOS attacks are usually done through bots that flood the network with connection requests or data which makes the system inoperable.
Call Tampering
Call tempering refers to the disruption of an ongoing call. Although call tempering is not as serious as other security threats, it is very bothersome.
The hijacker accesses the call stream and disrupts it by injecting additional noise packets. It becomes impossible to communicate in the presence of noise.
Vishing Scam Calls
Vishing is VoIP-based phishing. Hijackers make calls to seek important information like passwords and credit card numbers.
VoIP Fraud
The intruder uses your VoIP phone system and collects the revenue. Toll fraud is VoIp fraud in which the hijacker makes numerous international calls through your VoIP system.
Their goal is to get a share of the revenue generated by these calls. It is also known as International revenue sharing fraud (IRSF).

Malware and Viruses
Malware and viruses cause a lot of problems in the VoIP system. VoIP needs an excellent internet connection to work properly and the viruses consume network bandwidth and cause signal congestion. This security threat affects the quality of calls as the signal keeps breaking down.
These malicious programs can also result in packet loss. Moreover, they can make your system vulnerable to more damage by creating Trojan backdoors. These backdoors serve as entry points for intruders by bypassing authentication procedures.
How to Keep Your VoIP Network Secure?
You can ensure the security and privacy of calls by following the best practices.
Use Strong Passwords and two-factor authentication
You must ensure that your password is strong. It is advisable to change the passwords frequently.
Avoid using the same password for different accounts and encourage your employees to do so.
Moreover, work passwords should not include any personal information like home addresses.
Perform Security Assessment Regularly
A security breach that stays unnoticed does more damage than anything. You must perform security audits to detect and prevent attacks. It is recommended to hire an independent security agency to conduct a thorough security audit. The following things must be checked in a security audit.
● Firewall Performance: Ensure that the firewall is configured and can weed out hijackers. The firewall works well if no data packets are lost before reaching the target destination.
● Assessment of Patching Procedures: Ensure that both hardware and software of the VoIP system are not prone to Cyber attacks.
● Application Security: All applications used by the business must be thoroughly scanned. If you detect any security in an application, stop using it until the issue is resolved.
● Gateway Checks: VoIP gateways must have an effective security system in place
● Cyberattack Simulations: The security agency should test the ability of the VoIP system to detect and prevent any attempt of a data breach.
How to Choose the Right VoIP Provider?
The most crucial step towards ensuring the security and privacy of VoIP calls is choosing the best VoIP service provider. You can’t achieve your security goals simply by following VoIP best practices. VoIP providers and users must contribute to ensure a secure and safe communication system.
Consider the following factors before choosing a VoIP provider.:
Security Certifications
Your VoIP service provider must have all relevant security certifications. Some of the important ones are the following:
● Service Organization Compliance (SOC): The American Institute of CPAs created SOC2 to ensure secure data management. SOC2 criteria for managing customer data based on 5 trust service principles.
● Payment Card Industry Compliance (PCI): It helps ensure secure online payments through the card.
● HIPAA Compliance: It makes sure that patient data is well-kept and safe from intruders. It goes on to include voice notes and call recordings.
● ISO/IEC 20071 Compliance: This ensures that all security controls are effective and updated recently.
End-to-End Encryption
Ask the provider if they encrypt the data properly. Find out how the data is being encrypted. Sometimes encryption of data deteriorates the quality of the calls.
Staff Competency
Ensure that the staff of the VoIP service provider is regularly trained and retrained. No online system is completely resistant to cyber-attacks. The team of such a service provider must be vigilant and knowledgeable to face new challenges confidently.
Conclusion
In conclusion, VoIP is an efficient calling system as long as it is private and secure. Good VoIP practices help businesses to protect their data and systems from attack. You can ensure the security and privacy of your business calls by educating yourself about the problems and their solutions. If you are still trying to figure out where to start, seek our professional help from Venom IT to assess your risks and put in place the appropriate controls. Together, we can keep your business safe from security breaches.
In the ever-evolving telecommunications sector, change is inevitable. The Integrated Services Digital Network (ISDN), a technology that has been the sector’s backbone for decades, is facing its inevitable sunset. By 2025, the Public Switched Telephone Network (PSTN) circuits, including ISDN, will switch off indefinitely. In this blog, we will delve into what the 2025 ISDN switch off means, why it is happening, who will it affect, and how you should prepare for this transition.
What is the 2025 ISDN Switch Off?
ISDN, a circuit-switched telephone network, is on its way out. This move, to phase out ISDN, began in 2020 and continues as we shift toward fully digital networks. This not only affects phone lines, but other services connected to PSTN lines, such as alarms and CCTV. The hardware relying on this technology will stop functioning. Instead, you will need handsets capable of using Internet Protocol (IP) technology, transmitting digitally over broadband connections during phone calls.
Why is ISDN Being Switched Off?
The answer to this question lies in the age and outdated nature of ISDN technology. PSTN, the copper-wire-based telephone network, has remained unchanged since the start of public telephone networks and serves as the foundation for ISDN. While ISDN was revolutionary when it appeared in the 1980s, telecommunications capabilities have evolved significantly. Neither ISDN nor PSTN can manage the volume of sophisticated data needed in our increasingly digital world.
Who Will be Affected?
The ISDN switch-off will impact a range of businesses and individuals who still rely on this technology for their communication needs. Whether you are a small business or a large corporation, if your phone system relies on ISDN, it is urgent that you prepare to make the switch. Additionally, if you use non-voice services like alarms or CCTV connected to PSTN or ISDN lines, ISDN switch off UK will also affect these and will require you making the upgrade.
What to Do to Prepare
As the 2025 ISDN switch-off deadline approaches, you must take steps to ensure a smooth transition for your business. Here are the actions you might want to consider:
1. Explore VoIP Solutions
VoIP (Voice over Internet Protocol) will replace ISDN for voice communication. It is essential to research and select a VoIP provider that aligns with your business needs and budget. This will be a step forward, a more efficient and cost-effective solution, for your various communications needs.
2. Assess Your Business Needs
Decide what features you need from your new communications system. VoIP systems and cloud-based PBX solutions offer various features, so understanding your needs is crucial to make the right choice. Understanding your aims and capabilities will prove a fundamental part of your transition to VoIP
3. Check Internet Connection
Ensure that your internet connection supplies enough bandwidth to support your new VoIP system. A reliable internet connection is essential for high-quality voice communication. Assess your current Internet speed and bandwidth or work with your service provider to upgrade your plan or adjust your network for a smooth transition.
4. Plan for the Transition
Create a roadmap for transitioning from ISDN to VoIP. Depending on your existing infrastructure, this process can take weeks to complete. Consider using a provider who can help with the process. By creating a comprehensive roadmap, you can streamline the transition and ensure a successful switch.
5. Stay Informed
Keep abreast of updates and developments related to the ISDN switch-off. This ensures you stay informed about any changes to the transition process or deadlines. By actively seeking the necessary information from various reliable sources, you can stay updated on changes in regulations, deadlines, technology advancements, and VoIP service offerings.
Are PSTN and ISDN Both Being Switched Off?
Yes, there will be both an ISDN and PSTN switch off. The transition from these legacy technologies to modern, digital solutions is a global trend. As of September 2023, new ISDN lines are no longer available for order. The goal is to end the PSTN and ISDN networks entirely by December 2025.
In conclusion, the ISDN 2025 switch off is a significant milestone in the evolution of telecommunications. Embracing VoIP and other modern communication solutions is essential to future-proof your business and ensure uninterrupted communication. By taking initiative and preparing for the switch-off, you can minimise disruptions and harness the benefits of communication technologies. Do not wait until the last minute—start your transition to VoIP today to stay ahead in the ever-changing world of telecommunications.
So, what is multi cloud and what does this terminology mean? A multi cloud environment uses more than one cloud-based service, with those services supplied by different vendors. This kind of setup is most useful when organisations need to seek out certain features for a customer-facing application from multiple cloud providers.
When it comes to managing a multi cloud environment, it can be quite an in-depth and complex infrastructure which is best managed through professional intervention. Typically it will involve processes such as:
- Coordinating multiple cloud computing services across providers
- Addressing resource management
- Security considerations
- Compliance and relevant legal elements
- Data movement between cloud service environments.
Effective multi cloud management will help to enhance flexibility, efficiency, and recovery capabilities, using unique features of different cloud providers.
How does multi cloud storage work?
Organisations will typically manage multi cloud storage using dedicated controllers, which combine resources into a unified namespace and API. These allow centralised monitoring and management, ideally from your IT service provider, through a single dashboard. Storing data in the cloud provides flexibility and scalability, allowing compliance with diverse privacy laws. Automation is crucial for reducing errors and enhancing operational efficiency in managing applications across multiple clouds. This flexibility, helped by microservices and containerisation, allows organisations to select cloud providers based on universal standards rather than proprietary restrictions, creating the freedom for organisations to adapt to a more diverse set of multi cloud environments.
Multi cloud vs hybrid cloud
We use the terms “multi-cloud” and “hybrid cloud” to describe environments with multiple cloud configurations, but they have distinct meanings. Hybrid clouds involve the communication and transmission of data, applications, and services between public and private clouds, using a mix of on or off-premises private cloud resources and public cloud resources. Conversely, multi-cloud involves utilising resources from two or more clouds, typically public cloud services from different providers, supplying access to various service models. While you can hybridise multi cloud environments by incorporating private cloud resources with multiple public clouds, hybrid clouds specifically involve integrating or orchestrating different deployment types.
Benefits of a multi cloud strategy
Implementing a multi cloud strategy offers a huge range of advantages for organisations. Firstly and arguably most important, it mitigates risk by avoiding dependence on a single vendor, ensuring that downtime from one provider does not affect all services simultaneously. It enhances security through the distribution of cloud services across multiple providers, reducing the risk of attacks and optimising performance. It eases access to technology, allowing organisations to adopt solutions without heavy upfront costs and choose from a range of vendors. Customisation is another key benefit, enabling the best services from different cloud systems to align closely with specific business goals, thereby improving efficiency and return on investment.
Challenges of implementation
Building out a multi cloud environment still comes with challenges however. Finding the right cloud service for specific needs can require extensive research, as each cloud service varies in its support for applications and processes. The presence of workflow and management tools for each cloud service adds more complexity to the environment, although ultimately the use of cloud management tools can centralise infrastructure. Skill gaps across the range of IT services involved pose difficulty in finding individuals with the necessary ability for the evolving requirements. Data silos cause inconsistencies and unexpected outputs when applying business processes across separate locations. However, the use of containers and a hybrid environment can help to address this issue.
How an IT provider can help
A partnership with specialised cloud service providers will offer a dependable and robust framework, utilising the latest IT security technologies. Venom IT offers tailored solutions, full IT management, and collaboration with existing IT structures. We’ve been pioneering cloud solutions since 2009 and were among the first MSPs to supply GPU accelerated Hosted Desktop Solutions in the UK. If you’d like to speak to a cloud specialist about multi cloud environments, or anything else, please contact us here.
In today’s commercial landscape, the customer always comes first. They expect their queries to be resolved efficiently and promptly. However, when an issue arises, it’s not always easy to get it fixed in record time – that’s where support tickets come in.
Creating a support ticket is the easiest way to escalate a query to your tech team, but how you write a support ticket can be crucial. Not enough detail and your engineers won’t have a clue what they’re meant to do. Too much information and you could make matters worse by confusing your team and diverting their attention to an unrelated issue.
In essence, the way you convey the issue will set the tone for the resolution. If you want to learn how to write a support ticket, here are 6 steps you should follow.
1. Choosing the right subject line
First things first, you’ve got to pick the right subject line. By choosing the right keywords for your IT support ticket, you ensure it reaches its intended audience. Picking the wrong category could result in slower response times and frustration. Give your employees a few examples of issues and their expected categorisation to eliminate potential doubts. For example, rather than labelling a support ticket as an “urgent error” you can write “urgent: app crashes on login”.
2. Clear and concise description, proofread and tweak
Create a description that is clear, concise, and leaves no room for guesswork. Describe the problem from the end user’s perspective and the steps you took to diagnose the issue. Avoid using overly complicated jargon or abbreviations that could confuse the reader. Instead, use simple language and short sentences that specify the situation at hand. Creating a detailed yet direct description is one of the most fundamental steps in learning how to write a support ticket.
3. Additional supporting materials
Additional support materials, such as screenshots, time stamps, and exact error messages can help provide context. Support engineers don’t want to waste their time guessing what the issue could be; therefore, it’s important to illustrate the query with as many relevant support materials as you can find. Aside from providing additional data, you may also list the actions you’ve already tried, such as running a virus scan or restarting the web browser.
4. Summarise an expected outcome
Add a brief summary of the expected outcome towards the end of your IT support ticket to offer greater clarity on how the end user envisions the issue’s resolution. If applicable, consider implementing the steps you recommend for an accurate resolution process. Not only is this proactive, but it speeds along the process and ensures a more refined result. You can also add a realistic time frame in which the issue should be resolved to round things up.
5. Patience and respect
Showing patience and respect will cost you nothing and earn you everything. Don’t forget to treat your support techs with gratitude as it’s likely you’ll be working with them again in the future. Dealing with customer complaints can be extremely stressful; however, it’s important to remember you’re both on the same team. There’s no need to argue or shift blame, simply cultivate an environment that fosters openness and facilitates two-way communication.
6. Timely response to additional queries and providing feedback
During the resolution of the support ticket, you may find your customer has follow-up questions or additional queries. In this instance, it’s vital to demonstrate your attentiveness by responding to their concerns in a timely fashion. Once the customer issue is resolved, it’s important to collate feedback and liaise with your support engineer. By integrating feedback into the support ticket process, you can continuously improve your level of service and enhance customer satisfaction levels.
Still asking yourself, what should be included in the IT support ticket to make it perfect? Here’s a quick summary:
- Subject line: pick keywords that accurately summarise the issue at hand.
- Clear description: provide a detailed yet direct description of the problem.
- Attachments: include relevant files, screenshots, or attachments.
- Expected outcome: communicate the end user’s final expectations.
- Gratitude: don’t forget to show gratitude and practice patience.
- Follow-up or feedback: make a note of relevant follow-up queries or customer feedback.
Venom IT are a trusted and award-winning IT Support partner. Get in touch with our expert team today if you’re looking for new or alternative managed IT solutions.
Microsoft Azure is a popular cloud computing platform run by Microsoft, offering access, management, and development through global data centres. Azure allows you to support applications across multiple clouds, with customisable approaches. And as a public cloud platform, this includes services such as a service (PaaS), infrastructure as a service (IaaS), and managed database service capabilities. It works across web, mobile, cloud, and AI based services. Unlike other cloud-based services, Microsoft specifically designed Azure to help organisations manage applications and services across multiple channels.
Moving from on-premise to cloud
Microsoft’s disaster recovery system is fully able to ensure that your business can continue working during failures and outages. Azure offers Disaster Recovery as a Service (DRaaS), which will give you greater security than an on-premises data centre and does so at a lower maintenance cost overall, compared to running an efficient on-premises infrastructure. Moving from on-premises servers to cloud platforms will involve replicating copies of your existing data, migrating your operations to Azure, and decommissioning your on-premises resources. It’s a big decision to make and not one that should be taken lightly. However, the benefits are worth the commitment needed.
Azure migration plan
1. Inventory
Your first step will be examining which parts of your current system are to be migrated. By engaging in a thorough inventory of your servers and services, you will have a better understanding of how your operations work and how to migrate them. This will put you in the best position when developing your Azure migration strategy. Collaborating with your organisation’s various internal teams will ensure you get different perspectives on your computing capabilities and requirements.
2. Evaluation
Once you fully understand your organisation’s needs you can consider how best to migrate your systems to Azure. Luckily, Microsoft can help you with this, using their Virtual Machine Readiness Assessment tool. This supplies a checklist for moving your services to the cloud. Combined with Microsoft Assessment and Planning (MAP) toolkit, you can curate a transfer that considers your current infrastructure and capability, combined you are your performance requirements. It will also include your maintenance needs.
3. Customisation
Next, you will plan the best way to move your servers over, most likely splitting them between Microsoft Azure, which would benefit websites due to the speed of their data centres, Office 365, which would benefit productivity and communication workloads due to its collaborative interface, and a cloud-based operating system network, which is important for systems that require cloud computing or a virtualisation environment.
4. Migration
In this stage, you might start by transferring smaller systems to Azure. By delaying the transfer of your organisation’s more critical computing infrastructure, it will allow you to learn how to make use of the new tools at your disposal, while not risking jeopardising your core workloads with a system you are still adjusting to. We recommend considering best practices and allowing for margins of error during the learning stages of the azure cloud migration process.
Cloud Migration as a service
As a leading vendor of Azure migration services, Venom IT can help you undergo a full upgrade of your computing infrastructure and help you transfer your systems. We will help you to coordinate, deliver, and improve your organisation’s targets. We come highly recommended by our clients for whom we supply a bespoke and professional service, tailored to their needs and capabilities. We’ll help prepare your business to take full advantage of its innovation and maximise your return on investment, migrating on-premises applications, data, and infrastructure to a first-rate cloud-based network without disrupting your business.
Venom IT are a trusted and award-winning IT Support partner. Get in touch with our expert team today if you’re looking for new or alternative managed IT solutions.
What is DaaS and what’s got people talking?
Desktop as a Service (DaaS) is a very popular cloud computing solution that allows organisations to access a complete virtual desktop computing environment. Providers usually offer DaaS as a subscription-based package, which allows cost predictability and flexibility as different capabilities become necessary.
As a comprehensive desktop environment, you can imagine DaaS as an enhanced form of Software as a Service (SaaS), which only makes software applications available. Hosting computing infrastructure, network resources, and storage, and streaming them through a virtual desktop to any integrated device, DaaS is a necessity for every innovative, future-oriented organisation.
8 Core benefits of DaaS
1. Futureproofing: As technology evolves, virtual desktop users will be able to change their devices or core operating systems without disrupting their data infrastructure. Providers also invest heavily in potent security measures and compliance certifications, protecting your data. Finally, DaaS provides integration capabilities that ensure integration with any new devices that you introduce.
2. Scalability: Organisations can use DaaS to scale their infrastructure up or down, based on demand and necessity. Furthermore, you can do this without costly investment in new hardware over multiple disparate locations. The tiers of performance that you need are also straightforward to switch between, along with automatic upgrade and maintenance.
3. Cost: DaaS enables the streamlining of internal resources, while also lowering the requirements of supporting a physical infrastructure. Analysts estimate that this cloud-based strategy can save organisations between 30% and 50% over the course of four years. It also greatly reduces redundancies among resources, due to the elimination of unused hardware.
4. Flexibility: Being responsive in challenging times is one of the most important reasons for DaaS adoption. By buying a subscription or function-based services, businesses can adopt a pay-as-you-grow Operating Expenses (OpEx) payment model. This will make your organisation more responsive to the changing needs of your business at a much-reduced cost.
5. Security: Security burdens are shifted away from specific, individual devices and placed within a larger, more centralised infrastructure which maximises the protection available. You’lll no longer need to hold and back up your data on one vulnerable device, instead using an encrypted cloud environment, which is accessible only through multi-factor authentication.
6. Mobility: Virtual desktop providers may offer dedicated mobile apps that users can access on their smartphones or tablets, allowing them to access their organisation’s virtual desktops remotely. Also, DaaS is easily optimisable for the bandwidth capabilities of your devices and location while also often supplying offline access for specific applications and files.
7. Productivity: Enabling users to access an efficient computing environment, adopting DaaS will improve your organisation’s productivity. Allowing remote access and device independence, productivity is still high among both on-premises and remote team members. Also, using redundancy mechanisms, DaaS providers efficiently reduce downtime caused by maintenance failures and other common inconveniences or disruptions.
8. Ease of management: Your DaaS system will allow your IT administrators to enjoy a range of ease of management improvements. Providing organisations with a centralised management interface, you can manage multiple virtual desktops with reduced complexity. Crucially, the onboarding process is faster and more straightforward along with enhanced performance monitoring capabilities.
How a DaaS provider can help
Whether you are looking to transfer your organisation onto a DaaS infrastructure or just looking to change your current setup, VenomIT are among the leading providers of DaaS in the UK. Bringing you unparalleled knowledge, excellent customer support, and the latest cloud-based technology, we are immensely proud of the migration and maintenance services that we offer. We prioritise flexibility and dynamism without sacrificing any of the resilience or security that you should expect from your IT provider. Let us help you find the best solution for your computing needs and take a bold step in bringing your organisation into the future.
Venom IT are a trusted and award-winning IT Support partner. Get in touch with our expert team today if you’re looking for new or alternative managed IT solutions.
Cyber detection is an important part of cyber security, enabling a rapid response to detected threats so that attackers are not able to access sensitive data.
Some threats are known, and automated cyber detection programs can monitor for these and trigger automatic or manual responses when a threat is detected.
However, attackers are developing new ways to compromise secure systems all the time, and it is essential that threat detection and response should allow for these previously unknown attacks.
What are the different types of detection services?
There are many different types of detection services, and these are often referred to using three-letter acronyms (and in some cases, four-letter acronyms).
Some of the most commonly used TLAs in cyber detection services include:
- MDR: Managed Detection and Response, a professionally managed approach to detection
- TDR: Threat Detection and Response, an umbrella term used for cyber detection as a whole
- EDR: Endpoint Detection and Response, a form of cyber detection that focuses on endpoint data
- NDR: Network Detection and Response, a form of cyber detection that focuses on network data
- XDR: Extended Detection and Response, which uses broad algorithms to detect cyber threats
Commonly seen four-letter acronyms include SOAR (Security Orchestration, Automation and Response) and SIEM (Security Information and Event Management). These can refer to general approaches to network security, incident alerts, automated and manual responses.
ITDR (Identity Threat Detection and Response) is a specific discipline within the wider field of TDR, and is specifically concerned with protecting identity systems, e.g. by preventing unauthorised access using compromised employee credentials.
What is the difference between detection and prevention in cyber security?
Prevention is better than cure, and a well secured network will include measures to stop attempted cyber attacks at the network perimeter, e.g. a network firewall and incoming email scans.
Cyber detection is a little different. It’s about identifying threats that exist on your network, so that any active exploits can be ended and repaired.
This does not mean that your preventative measures are inadequate (although it may indicate that a review of network security is needed), but can be a consequence of newly developed exploits and newly discovered zero-day vulnerabilities.
Managed detection and response (MDR) puts cyber detection in the hands of experts like Venom IT, so any newly found vulnerabilities can be patched quickly and data integrity restored.
What is the difference between TDR and EDR?
TDR (Threat Detection and Response) is a general term for detecting and mitigating cyber threats and can include specific disciplines like EDR, NDR and ITDR.
EDR (Endpoint Detection and Response) is a specific niche within TDR and focuses on endpoints such as computers, laptops, smartphones, IoT-enabled devices, peripherals and wireless devices.
By creating a point of connection from the outside world to a business network, these endpoints represent a common target for cyber attacks – EDR recognises this exposure and uses it as a starting point for cyber detection, helping to prevent attacks at their source.
How can cyber detection services help my business?
Cyber detection services are an essential investment for any data-driven business, to reduce network downtime, protect sensitive data and prevent enforcement action from the ICO.
Venom IT’s managed detection and response services give you peace of mind that your business is professionally protected against cyber attacks through a convenient Security as a Service (SECaaS) subscription plan.To find out more, contact Venom IT today or read our guide to Cyber Security Basics.
Just as in medicine, cyber threat prevention is better than cure. A vigilant approach to cybercrime prevention can keep would-be hackers from gaining access to sensitive data or maliciously encrypting files as part of a ransomware attack.
Preventing cyber security attacks is not easy. New exploits and vulnerabilities emerge all the time, and cyber security prevention is a race between criminals and ‘ethical hackers’ whose goal is to identify weaknesses so that they can be proactively patched.
Venom IT’s cyber attack prevention services form part of our Managed Cyber Security solution, and can be accessed by businesses through a flexible and convenient SECaaS (Security as a Service) subscription.
What are the different types of prevention?
Cyber threat prevention depends on several layers of proactive measures aimed at preventing cyber security attacks.
These include:
- Secure configuration of network hardware and endpoints
- Network perimeter security (e.g. firewall and port blocking)
- Adequate user access control and identity protection
- Malware/virus monitoring and responsive protection
- Vulnerability testing, penetration testing and patches
An ongoing approach to cyber security prevention involves finding zero-day vulnerabilities – new weaknesses that could be used by a hacker to enter your network via the back door – and installing patches that close these programming loopholes before they are exploited.
What does a cyber security service provider do?
As a SECaaS cyber security service provider, Venom IT adopt a comprehensive cybercrime prevention plan.
We verify user identity and access, filter out unauthorised connections, block malicious content from entering your network, and test new security controls on an ongoing basis.
The cloud model of our SECaaS cyber attack prevention service means you benefit from ever-evolving protection, giving you state-of-the-art safeguards to keep your organisation a step ahead of the hackers.
How do cyber threat prevention services help my business?
Cyber attack prevention helps your business in mission-critical ways:
Prevent Downtime
Keep critical business networks available and protect data against malicious encryption, ransomware attacks and other exploits.
Reduce Costs
Vigilant cybercrime prevention reduces the cost of responding and repairing in the event of an attack, by ensuring malware does not take hold of your network.
Improve Compliance
Avoid enforcement action from data commissioners by protecting individually identifiable data against leaks and theft.
How high is the cyber threat risk?
Preventing cyber security attacks is an existential issue for many businesses. High-profile ransomware attacks in recent years demonstrate that even big brands are not immune to cybercrime and can experience protracted downtime following a successful exploit.
UK Government research shows that in 2022-23, one in three businesses (32%) experienced a cyber attack or breach in the previous 12 months, rising to three in five (59%) medium-sized businesses and nearly seven in ten (69%) large businesses.
Just one in five (21%) businesses of all sizes have a formal cyber incident response plan in place, highlighting the need to prevent cyber attacks in the absence of a plan for how to respond.
Venom IT provide comprehensive cyber attack prevention, detection and recovery services as part of our flexible subscription-based SECaaS model – contact us today to find out more.
How do you protect your data? What would you do if your organisation was under attack? How long until all systems are up again?
These are all crucial questions that you should know the answers to. In fact, these answers will paint a clear picture of your strategy, so it’s best to nail those key cyber security questions before you settle on an IT provider.
What Cyber Security services should an IT provider offer?
Your Security as a Service provider, or SECaaS for short, should offer a comprehensive range of cybersecurity services. Here are just a few:
- Penetration testing: authorised and simulated cyber attacks on a computer’s system or network.
- Firewall management: monitoring firewalls and setting rules or policies to ensure safety.
- Vulnerability assessments: evaluating and prioritising the vulnerabilities in your system.
- Endpoint protection: identifying and safeguarding endpoints, such as laptops, smartphones, and other devices.
- Threat intelligence: analysing data to understand a hacker’s motives, behaviours, and goals.
- Incident response: processes and technologies used to respond to cyberattacks or breaches.
Cyber Security FAQ for your IT company
Asking the right kind of cyber security questions for IT department can highly influence your decision-making process. To ensure you cover the cyber security basics, we recommend you ask the following:
Q. What cybersecurity strategies are right for my business?
There is no “one-size-fits-all” approach when it comes to cyber security services. On the contrary, your strategy should feel bespoke to the needs of your organisation. Ideally, your IT provider will conduct a vulnerability assessment and identify the unique needs, risk profile, and operational environment of your organisation. Most IT providers will follow a similar framework: evaluating risk assessment, ensuring goal alignment, facilitating compliance, and implementing proactive security measures.
Q. How often will you perform IT security audits?
The frequency of your IT security audits will depend on the size and complexity of your organisation, as well as the pace of the evolving threat landscape. Once or twice a year is a reasonable starting point. Other times to schedule IT security audits are after major events such as the implementation of a new data system or post-data breach.
Q. Where will my data be stored and protected?
Choosing a place to store and protect your data involves careful consideration. More specifically, you’ll need to think of factors such as security, compliance requirements, and accessibility. For example, cloud storage typically provides greater scalability and flexibility; however, it also fosters a greater reliance on third-party providers and may increase your vulnerability.
Q. How and who does risk assessment?
Your IT service provider should have several risk assessment professionals on their team. These individuals are in charge of defining security objectives, identifying assets, monitoring threats, calculating risks, documenting their findings, and implementing new controls or enhancing existing ones.
Q. Is there any training to offer our business?
Sophisticated security is only as strong as your team’s awareness; without employee training, cyber attacks can penetrate even the most advanced measures. Implement a culture of cyber security awareness and reduce the risk of data breaches by training your employees. Your IT provider should offer activities like simulated phishing exercises, awareness campaigns, and security awareness workshops.
Q. What happens if a threat is detected, or data is compromised?
In the event of a serious threat or data breach, coordination and urgency is of the essence. Your IT provider should detect the issue, understand the extent of the threats, and isolate the affected systems. Once relevant stakeholders and authorities are notified, your IT team should begin implementing remediation measures. The faster they can mitigate the impact of security incidents, the better they can protect the organisation’s reputation.
Q. How does your team keep on top of trends and new threats?
Just as new cyber threats are constantly emerging, so are the innovative solutions employed by SECaaS teams. If you want to outpace evolving risks, you’ll need to find a provider who demonstrates these qualities. The best way to find out is by asking relevant cyber security questions. You can inquire about their certification programs, industry involvement, research initiatives, and continuous monitoring capabilities.
Based on the answers to your cyber security FAQ, you can determine whether they are the right IT provider for your organisation.
Almost all companies expect their employees to conduct work online while keeping sensitive data safe. But how can they uphold these expectations when faced with scenarios like remote work, bring-your-own-device policies, or the increasing complexity of cybersecurity threats?
To address these challenges, many enterprises choose to invest in a hosted virtual desktop setup. This approach allows employees to access their workplace desktops from any device or location while offering a seamless user experience and heightened security stance.
In this guide, we’ll explore the basics of desktop virtualisation, and why it’s quickly cemented itself as a cornerstone of many organisation’s cybersecurity and workstation strategies.
What is desktop virtualisation?
Desktop virtualisation is essentially a virtual copy of a workstation desktop that allows the end user to access their applications and software from anywhere in the world (and at any time). Rather than depending on the static location of their work desktop, they can log in from a connected device and benefit from a digital workspace.
What is a hosted desktop?
Hosted Virtual Desktops, or HVDs for short, are a type of cloud-computing model that allows users to outsource desktop virtualisation to a third party. Hosted virtual desktop providers offer DaaS solutions that facilitate an organisation’s access to workplace data, software, and applications from a remote device.
All that is needed to access a hosted desktop is a high-speed internet connection and reliable hosting provider. Since no confidential data is stored on the hardware itself but rather a protected HVD network, businesses can rely on an added layer of security while cutting down on hardware costs.
How can businesses use hosted desktop services?
Desktop virtualisation helps organisations increase flexibility, reduce expenses, streamline productivity, and bolster their security stance. From a centralised hosted virtual desktop provider, businesses can offer hundreds and thousands of employees a uniform application hosting experience. Here are a few notable benefits:
Remote work and flexibility
Remote desktop solutions are particularly useful for companies that embrace remote working, opt for a hybrid work model, or operate various branches across the globe. It offers flexibility for organisations with a distributed workforce as employees can collaborate regardless of their geographical location.
Cut down on costs
Products like a citrix hosted desktop can be very cost-effective when implemented correctly. Rather than investing in unnecessary hardware and software subscriptions, organisations can manage everything from a single server.
Streamline productivity
Hosted desktops encourage productivity and streamline procedures by providing quick solutions to a vast number of user experience problems. There’s no need to spend time or money fixing individual server issues, as IT departments can use desktop virtualisation to update security patches and deploy tasks simultaneously.
Improve security measures
Implementing individual security measures for thousands of users is not only tedious but potentially risky. Imagine your employee loses their laptop, and with it, the company’s confidential data. Rather than suffering a security breach and implementing a risk mitigation plan, a hosted desktop reduces the overall level of risk.
What other desktop virtualisations are available?
Within the realm of desktop virtualisation, there are various models to choose from. The type of desktop services an organisation needs will vary in accordance with their bespoke requirements. Here are some of the most common types:
Hosted virtual desktops
As mentioned above, hosted virtual desktops offer the convenience of outsourcing desktop virtualisation services to a cloud computing provider. These specialised companies take over daily maintenance tasks and ensure servers are running without fault. This option is suitable for SMEs that don’t want to invest in in-house remote desktop solutions yet need scalable and cost-effective solutions.
Virtual desktop infrastructure
Virtual desktop infrastructure, or VDI for short, offers a similar service as HVD while providing organisations greater control over their virtualisation stack and infrastructure. This option is ideal for larger enterprises that need more customisation to meet their organisational requirements.
Remote desktop services
Remote desktop services are a type of Microsoft infrastructure model that enables Windows software to run securely on a centralised server while allowing employees to access applications from various devices. This type of desktop virtualisation is beneficial for businesses that prioritise centralised application delivery.
Local desktop virtualisation
Local desktop virtualisation involves running virtualised desktop environments on individual and local servers. This way, users can access multiple operating applications or systems from a single physical device. This option is viable for organisations that can handle resource-intensive tasks on isolated workspaces and don’t need a continuous network connection.